The Oracle Database Security Assessment Tool (DBSAT), currently in version 3.1.0 (January 2024), is a command-line tool focused on detecting potential security vulnerabilities. Its greatest scope occurs within the database but it also inspects operating system and network components (listener) in search of failures.
The tool provides insight into the current status of users, roles, permissions, and security control policies to promote successful approaches to mitigating potential security risks.
What’s new in DBSAT 3.0 ?
New checks added in DBSAT 3.0 include the newly introduced Oracle Database 23c SQL Firewall, auditing-related issues, sensitive data and transparent sensitive data protection, and a wealth of other checks necessary for any security-conscious organization. Remarks and recommendations are updated to make them clearer and actionable.
Desupport notices list database features and parameters that are reaching or have reached their end-of-life so you can take proactive measures to phase out their usage. DBSAT Discoverer also added support for India’s permanent account number (PAN) and the unique identification (Aadhaar) number.
From its beginning, DBSAT offered a distillation of decades of security experience, checking configuration issues that might introduce unnecessary risk. Until now, DBSAT clearly identified checks that were related to security frameworks like the DISA STIGs, Center for Internet Security (CIS) benchmarks, or data privacy regulations like GDPR. However, no checks clearly indicated that they were Oracle best practices. DBSAT 3.0 fixes that issue: Findings that are Oracle best practices are now clearly identified.
When is DBSAT not enough?
DBSAT is a simple standalone tool that helps assess the security configuration of a single Oracle Database. What if you want to automate assessments across your fleet, track deviations from approved baselines, get alerts, keep history, and compare all in one interface? Use Oracle Data Safe or Oracle Audit Vault and Database Firewall to go the extra mile in assessments.
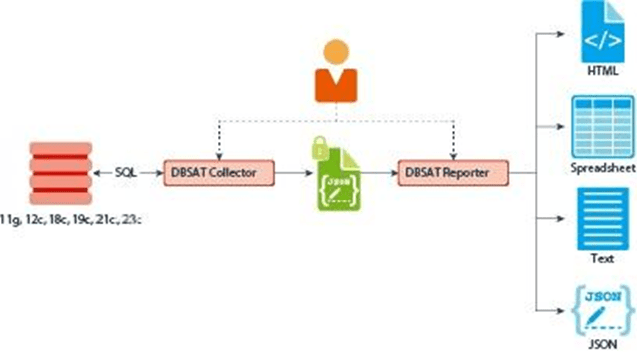
The DBSAT is made up of two components:
DBSAT Collector: Responsible for executing SQL queries and operating system commands that collect the data to be evaluated. The data is stored in a file that is later used by DBSAT Reporter in the analysis phase.
DBSAT Reporter: Responsible for analyzing the collected data and generating reports of findings and recommendations in files of multiple formats such as HTML, Excel and Text.
The main benefits of using DBSAT are:
- Quick identification of database security configuration errors;
- Recommendations based on best security practices;
- Reduction of the amplitude of an attack and exposure to risk.
DBSTAT works on Oracle database 11.2.0.4 and later versions including multitenant and cloud environments. The supported platforms are:
Oracle DBSAT runs on:
- Solaris x64 and Solaris SPARC64
- Linux x86-64 and Linux 64-bit Arm
- Windows x64
- HP-UX IA (64-bit)
- IBM AIX (64-bit) and Linux on zSeries (64-bit)
Its use is very simple and consists of downloading the MOS file (My Oracle Support – Doc ID 2138254.1), unzipping it, and running the script to collect and report security vulnerabilities. DBSAT is a lightweight utility that does not hamper system performance while running.
Running DBSAT Collector:
For DBSTAT to collect all the data and perform a complete validation, it must be executed from the database server, as some operating system commands are executed to collect data that cannot be obtained from the database. DBSTAT must also be run with an operating system user that has read permission on ORACLE_HOME files and directories for data to be collected and processed properly.
Collections in the database are carried out mainly on data dictionary views, so the user that will be provided in the connection string to the database must have sufficient permissions to select data from these views.
Collector Prerequisites
To gather all necessary data, run the Oracle DBSAT Collector on the database server. The collector uses operating system commands to gather process and file system information that the database alone cannot provide. Besides, the Oracle DBSAT Collector must be run as an OS user with read permissions on files and directories under ORACLE_HOME using SQL*Plus (through Oracle Database or Instant Client) to collect and process file system data using OS commands.
The Oracle DBSAT Collector collects most of its data by querying database views. It must connect to the database as a user with sufficient privileges to select from these views. Grant the DBSAT user the following privileges:
- CREATE SESSION
- READ or SELECT on SYS.REGISTRY$HISTORY
- Role SELECT_CATALOG_ROLE
- Role DV_SECANALYST (if Database Vault is enabled or if Database Vault Operations Control is enabled)
- Role AUDIT_VIEWER (12c and later)
- Role CAPTURE_ADMIN (12c and later)
- READ or SELECT on SYS.DBA_USERS_WITH_DEFPWD
- READ on SYS.DBA_AUDIT_MGMT_CONFIG_PARAMS
- READ on SYS.DBA_CREDENTIALS
- EXECUTE on SYS.DBMS_SQL
Syntax for running the DBSAT Collector:
$ dbsat collect <database_connect_string> <output_file>
[oracle@oracle-db-lab dbsat]$ ./dbsat collect "c##test1/test#123" /home/oracle/dbsat/collect/output_ORCL Database Security Assessment Tool version 3.1 (Jan 2024) This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Connecting to the target Oracle database... SQL*Plus: Release 19.0.0.0.0 - Production on Fri Jan 19 23:52:20 2024 Version 19.19.0.0.0 Copyright (c) 1982, 2023, Oracle. All rights reserved. Connected to: Oracle Database 19c Enterprise Edition Release 19.0.0.0.0 - Production Version 19.19.0.0.0 Setup complete. SQL queries complete. OS commands complete. Disconnected from Oracle Database 19c Enterprise Edition Release 19.0.0.0.0 - Production Version 19.19.0.0.0 DBSAT Collector completed successfully. Calling /u01/app/oracle/product/19.0.0/dbhome_1/bin/zip to encrypt output_ORCL.json... Enter password: Verify password: adding: output_ORCL.json (deflated 86%) zip completed successfully. [oracle@oracle-db-lab dbsat]
By default, the file will be generated and compressed with a password. However, we can omit the need to enter a password by adding the -n parameter in the best collect call. However, considering information security, this is not recommended.
Running DBSAT Reporter:
The prerequisite for DBSAT Reporter is that Python 2.6 or higher is installed on the server where the report will be generated. By default it is already installed in most UNIX environments.
To confirm the existence and version of Python run:
python -V
Syntax for running the DBSAT Report:
dbsat report [-a] [-n] [-x <section>] <input_file>
The Reporter supports the following command-line options:
- -a
Runs the reports for all the database accounts.
- -n
Specifies no encryption for output.
- -g
Shows all grants including common grants in a pluggable database.
- -x
Excludes a section from the report.
Valid sections are:
- USER : User Accounts
- PRIV : Privileges and Roles
- AUTH : Authorization Control
- CRYPT : Encryption
- ACCESS :Fine-Grained Access Control
- AUDIT : Auditing
- CONF : Database Configuration
- NET : Network Configuration
- OS : Operating System
To exclude multiple sections use a comma-separated list, for example:
-x USER,PRIV
Or:
-x USER -x PRIV
Omitting this option will include all sections of the report.
The same path name is used to generate the report files produced by the Reporter in HTML, Excel, JSON, and Text formats with the appropriate file extensions.
Run the Reporter.
[oracle@oracle-lab dbsat]$ export JAVA_HOME=/u01/app/oracle/product/21.0.0/dbhome_1/jdk [oracle@oracle-lab dbsat]$ export PATH=$JAVA_HOME/bin:$PATH [oracle@oracle-lab dbsat]$ ./dbsat report -n output_ORCL Database Security Assessment Tool version 3.1 (Jan 2024) This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. DBSAT Reporter ran successfully. [oracle@oracle-lab dbsat]$
DBSAT Reports:
DBSAT produces output in various formats for various audiences and purposes. An HTML report, for example, provides detailed results in an easy-to-navigate format using links while a Spreadsheet report provides a high-level summary of each finding, as well as allowing you to manipulate columns by adding new ones for your purposes and prioritization.
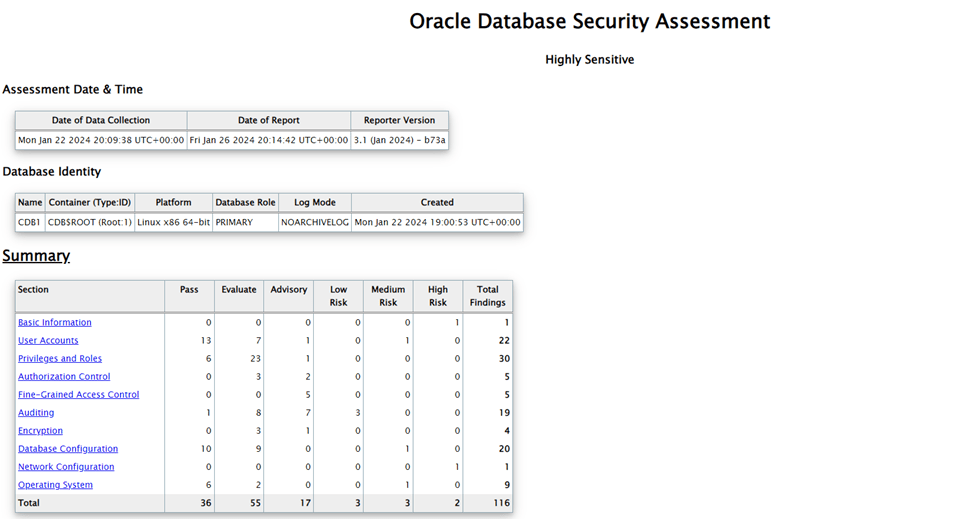
Example of a DBSAT summary in HTML:
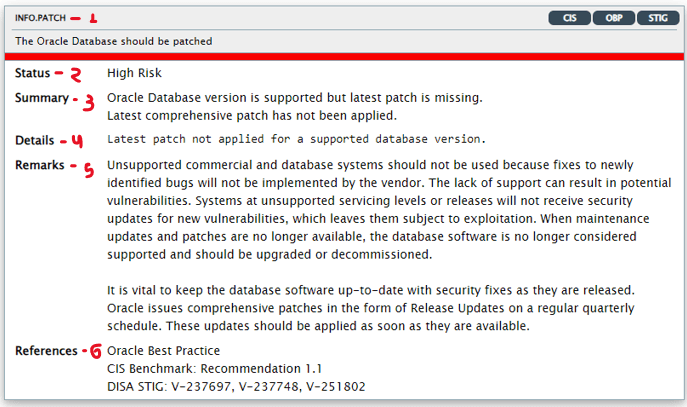
1. Rule title and unique ID:
The ID has two parts: the prefix identifies the report section and the suffix identifies the specific rule.
2. Status:
Status can be used to define the prioritization of indicators, where a high-risk finding requires immediate action while a low-risk finding can be scheduled and adjusted with less priority.
- Pass: No errors or risks identified;
- Evaluate: It is necessary to carry out a manual analysis to identify the degree of risk;
- Some Risk: Low risk;
- Significant Risk: Medium rich;
- Severe Risk: High security risk;
- Opportunity: Additional opportunities to improve security using additional technologies.
3. Summary:
Discovery summary.
4. Details:
Provides detailed information to explain the discovery.
5. Remarks:
Explains the standard used to evaluate the results found. It can also explain recommended actions for remediation if a risk is reported.
6. References:
Lists the discovery based on the CIS Oracle Database Benchmark, DISA STIGs, Oracle Best Practices.
I hope this article helps you.
See you in the next article.
Disclaimer: “The postings on this site are my own and do not necessarily represent my current employer positions, strategies, or opinions. The information here was edited to be useful for general purpose, specific data, and identifications was removed to allow reaching a generic audience and to be useful.